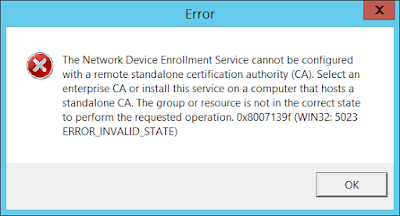
Auto-enrolled OCSP certificates
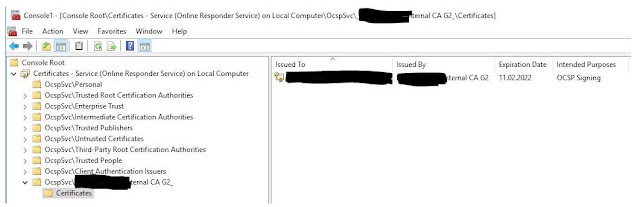
In a Microsoft AD CS based platform including an Enterprise CA, it is quite common to setup the OCSP responder to automatically enroll for and renew the required certificates. This is usually achieved creating a custom OCSP Response Signing certificate template and granting the computer(s) where the OCSP Responder runs the required enrollment rights. There are 2 interesting things to note in such a setup: 1. The OCSP Responder computer objects only require "Read" and "Enroll" rights on the template, although it feels like Windows auto-enrollment no "Auto-enroll" right is required. 2. The OCSP Response Signing certificates issued via this mechanism are stored in the service specific certificate store, and not in the Computer certificate store (as would be the case if they were generated on a different way). To view them run the mmc.msc snap-in and then go to File > Add/Remove snap-in > Certificates > Service Account > Local computer > Online ...