Remote shell not accepting requests
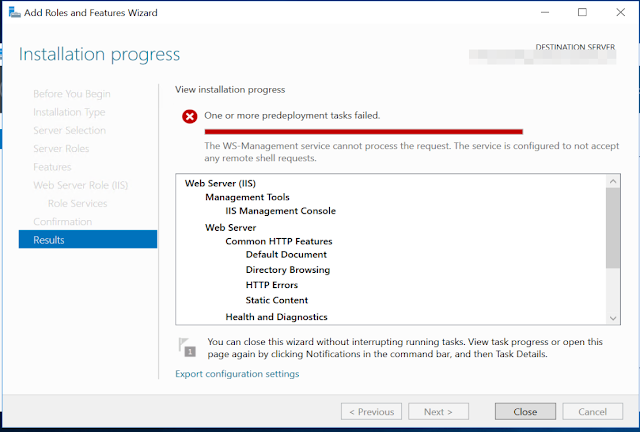
The following is one of the most common error messages nowadays when trying to install roles and/or features via Server Manager: When attempting installation via Server Manager the following error message is displayed: " The WS-Management service cannot process the request. The service is configured to not accept any remote shell requests " When trying via PowerShell a similar error message is displayed. There are a number of guides out there resolving it via Local Group Policy Editor, changing netsh settings etc., but in my experience, in locked down environments where policies are set via GPO etc. some of those don't work and often it is also the case that policy changes are not properly persisted even if GUIs or PowerShell commands tell otherwise. The most reliable way of temporarily (until policies are re-applied) working around it, is as follows: If you are using Server Manager close it Open the registry editor ( regedit.exe ) and look for the following entry: ...